Networks
The majority of computer systems involve a form on network, often the internet. A computer network is a collection of interconnected computers with the capacity to communicate with one another, whether that be through a wired or wireless connection. They are great as they can allow a user to access their files on any computer within the network and can share devices, files and software. However, it does mean that each computer is reliant upon the network and if one computer gets a virus, then it can be spread very easily.
This topic covers:
-
Types of network
-
Networked structures
-
Protocols
-
Ip addresses
-
Networking Hardware
Types of network
Networked computers can share devices, files and services and are able to communicate with one another. However, the way this works depends on the type of network.
Local area network (LAN) –
A LAN is used over a small geographical location, such as a school. They are almost always connected via wires, as this increases transfer speeds. They are more secure than a WAN and require no extra communication device. They are also wired from one central point.
Wide area network (WAN) –
A WAN is used over a large geographical area. They are almost always wireless, as their reach is huge and therefore require external communications. The most common example of a WAN is the internet. This means that the internet can be accessed in any country. WANS are more susceptible to data interception, as they pass over different networks owned by different people. Consequently, a ‘man-in-the-middle- attack can happen, where data is edited or stolen. Hence, encryption exists.
Topologies
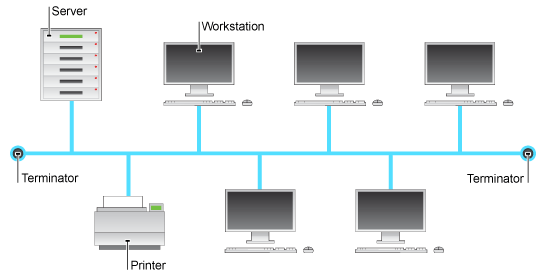
Bus/Line:
Each device in the network is connected to a central cable via a spur. At each end of the cable is a terminator These absorb signals so that the they don’t reflect down the cable, as this would cause collisions and therefore a loss and disruption of data. They are mainly used in LAN’s.
When drawing this topology, always remember to include at least 2 different clients, at least one server and at least one external device (like a printer) all connected to a main cable, with the terminators drawn in at each end. Each part must be clearly labelled.
Some advantages are:
-
They are simple to connect devices to
-
Uses a fairly low amount of cables, reducing costs
-
Easy to extend
-
If one node fails, the network can continue fine
However, some disadvantages are:
-
If the main cable is disrupted or broken, the whole network goes down
-
Despite the terminators, collisions do still happen and result in packet loss
-
As more devices are added, the network slows down, hence why it is only really suitable for LAN’s.
-
It can be difficult to locate faults and problems.
Ring
Each Node is connected to the previous one and the next one, resulting in a ‘ring’ - like structure. This means that data travels along the continuous pathway, with each node it passes handling every packet. Data can travel clockwise, anticlockwise or bidirectional.
Some advantages are:
-
Under heavy traffic, it performs more reliably than a bus topology
-
Doesn’t require a central node
-
It is easy to detect faults and problems
-
It is fairly easy to add or remove new devices.
The disadvantages are:
-
If one node has a problem, then it affects the entire network
-
When adding devices, the network can be affected
-
Bandwidth is shared between all devices
-
Can only be used in a LAN
Star:
Each node is separately connected to a single connection point, either a hub or a switch. Data is sent into the hub, where it is processed before continuing to its destined location.
The advantages are:
-
It is good for larger networks
-
Nodes/devices can be easily implemented without the network going down
-
As more devices are added, the network doesn’t really slow
-
If one node malfunctions, the others can remain active
The disadvantages are:
-
If the central hub fails, the whole network fails
-
Many cables are required as each node is connected separately, meaning it can be very expensive.
Protocols
When 2 people who speak different languages attempt to communicate via their own language, they can’t communicate. They require a translator, or attempt to use hand gestures etc. Computers work in the same way; they cannot communicate without following a set of rules. These rules are called protocols. You also need to know about the term ‘handshaking’. Before even a byte of data is sent, it’s important for devices to agree on a protocol, else they won’t understand one another. Consequently, a handshaking signal is sent from one device to another, until they agree on a protocol.
Protocol Stacks
Having a layered protocol allows for the separation of logic, so that problems may be processed separately. It also means protocols can be swapped out at different parts of the stack. The most modern commonly used stack is the TCP/IP stack.
The TCP/IP stack is split, from the bottom up, into the hardware layer, the network layer, the transport layer and the application layer. Other than the hardware layer, there is a protocol choice at each layer, providing different properties for the packets sent based off which is picked.
Data is added to the packets header as it travels down the stack, before being put on the network hardware, where it is transported to its destination. Once it gets there, it is placed back into the stack, with each section dealing with a part of the header.
Types of protocol
-
HTTP -Allows for resources from a web server, like images and text to be transmitted over the network and be presented to the client. Called Hypertext transfer protocol.
-
FTP – Used when downloading or writing a file from one location to another via the internet. Called File transfer protocol.
-
SMTP – Used for sending emails between different systems via the internet. Called Simple mail transfer protocol.
-
TCP – Provides reliability when delivering packets online, by having error-checked streams of packets over a network. A sequence number is generated so that the packets can be reorganised into the correct position at its destination. This protocol also checks the packet has arrived and resends it if no confirmation is received. Called Transmission control protocol.
-
IMAP – Used for email retrieval over the internet and allows multiple users to access the same mailbox at once. Called internet message access protocol.
-
DHCP – Used to dynamically allocate an IP address to devices on a network. This reduces the need for a user to configure it automatically. Called Dynamic Host Configuration Protocol.
-
UDP – An alternative to TCP. It still sends emails, but much faster. This is because there is no error checking or resending of lost information. Therefore, it is unreliable and unsuitable for packets that can’t lose data.
-
IP – Called the internet protocol. Each device is assigned a unique IP address, in the form 111.111.1.1, with each number varying up to 255. This address of both the sender and receiver is included when data is transmitted over a network.
Hardware
For computers to work together in a network, some hardware is required. We need to know about the main ones that enable a basic network setup.
Network Interface Card
Responsible for placing packets onto the network’s cables, this allows computers to connect to a LAN. All computers in your school will probably have one of these Most modern motherboards have these integrated anyway. For a wireless network, a wireless interface card is needed, however as before, most new devices have these integrated anyway.
Hub
Used in star topologies, by allowing each device to be connected via a single cable. They work well in small networks, but no so well in larger ones since they repeat all packets to every device. However, they are cheap and so can be used in connection with a switch in larger networks
Switch
In a process called routing, a switch determines which port contains the destinated address. The address they us is called a MAC (media access control) rather than an IP address. This is an address hard-coded into every device in the world, which cannot be changed. They take the format of 12 hexadecimal numbers.
Router
Like switches, they route packets to the correct port, but are used for a different purpose. They allow for different parts of a network to be connected, such as connected the internet to a LAN. And use IP addresses rather than MAC addresses. They are necessary for connecting to a WAN and hence why most households have one.
Wireless
Whilst offering portability, these kinds of networks give far less security and performance when in companion to wired networks. Most mobiles and tablets connect to wireless LAN’s in our own households, which is essential for accessing the internet via Wi-Fi. They save expense by limiting the use of cables, but are unreliable, with distance and even weather affecting performance.
Open networks
Open networks are networks that anyone can connect to without a password, for example at a local coffee shop. The problem with them, is that the data sent across the network isn’t encrypted, meaning that it can be easily intercepted and so important information like banking details should be avoided when using this kind of network.
Private wireless LAN
These are protected by encryption and can only be decrypted using the encryption key, which is shared only with the sender and receiver. When networks (WEP, or wired equivalent privacy) use a static key, the key doesn’t change and so is vulnerable to cracking (discovering the key), but others (WPA2, or WIFI protected access) use a protocol to change it during communication, making it far more difficult to crack.